
by digitaloperatives | Jul 18, 2023 | Security News
Friends, cyber-citizens, netizens – lend me your IPs. Here at Digital Operatives LLC, we see cloud security issues regularly. Sometimes we find real vulnerabilities in customer cloud implementations. Other times, issues arise simply because of password reuse....
by digitaloperatives | Oct 19, 2018 | Research, Services
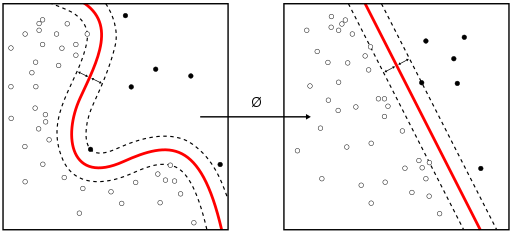
Reading /r/netsec today, I happened to come across this recycled old 2017 blog post from Cisco security about detecting malware by applying machine learning to encrypted communications. Admittedly, it’s an interesting idea. At some point malware started using...

by digitaloperatives | Oct 10, 2018 | Capture the Flag, Security News
On Monday we became a tenant at the shared office provider WeWork. According to their website, “WeWork is a global network of workspaces where companies and people grow together.” We needed something more flexible while our new corporate office is being...
by digitaloperatives | Sep 1, 2018 | Research
At Digital Operatives, sometimes our eyes are bigger than our stomach. We’re a small, focused security company trying to help the nation improve in cyber-security. Fundamentally though, we’re an “ideas” company. We come up with ideas, and as...
by digitaloperatives | May 15, 2018 | Products, Security News, Services
Every blog author should ask themselves at some point, who is the target audience for this blog post, website, or tool? Digital Operatives started out as a niche cyber-security company doing advanced research and development somewhat before the term...




