The Codegate 2013 YUT Preliminary capture-the-flag event wrapped up last week on March 03, 2013. Congratulations to the European NOPSled Team for winning the challenge and congratulations to all who qualified to participate in the final challenge in Korea on April 3rd.
A contingent from Digital Operatives participated with a small team including friends. We enjoyed attempting to solve the many interesting challenges in this CTF. One in particular, solved by Joshua Dugie, was a great little problem. Below is his writeup of the challenge.
We are given a file, 396c983d4290901e4060ffe25e7c0eb3, with the instructions, “Find the key.”
The file is a 7-Zip archive with a single file inside, DNA.png. DNA.png is a 1×992 PNG image with single color pixels in a column, separated by two black pixels.
To extract the information from this image, you can use the Python Imaging Library.
#!/usr/bin/python
import PIL.Image
# get DNA.png pixels
pixels = []
f = open('DNA.png', 'rb')
im = PIL.Image.open(f)
vpixels = im.getbbox()[3] + 1
for i in range(0, vpixels, 3):
pixels.append(im.getpixel((0,i)))
f.close()
# convert pixel tuples to data
data = ''
for pixel in pixels:
for x in pixel:
data += chr(x)
# write out the data
f = open('dna.bin', 'wb')
f.write(data)
f.close()
dna.py
Running file on the resulting data gives “dna.bin: x86 boot sector, code offset 0x5” and xxd can confirm (see the bytes 55aa at offset 0x1fe):
jdugie@machine:~$ xxd dna.bin 0000000: ea05 00c0 078c c88e d8b8 00b8 8ec0 b9ff ................ 0000010: 07be 4700 bf00 008a 0426 8805 4726 c605 ..G......&..G&.. 0000020: 073c 0074 0547 46e9 edff b800 108e c0bb .< .t.GF......... 0000030: 0000 b402 b001 b500 b102 b600 b200 cd13 ................ 0000040: 72e8 ea00 0000 1052 6564 5374 6172 4f53 r......RedStarOS 0000050: 2042 6f6f 7469 6e67 2e2e 2e00 0000 0000 Booting........ 0000060: 0000 0000 0000 0000 0000 0000 0000 0000 ................ ... 00001d0: 0000 0000 0000 0000 0000 0000 0000 0000 ................ 00001e0: 0000 0000 0000 0000 0000 0000 0000 0000 ................ 00001f0: 0000 0000 0000 0000 0000 0000 0000 55aa ..............U.
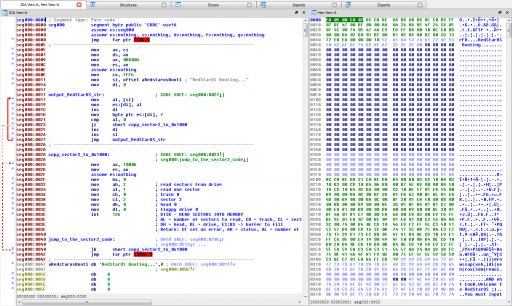
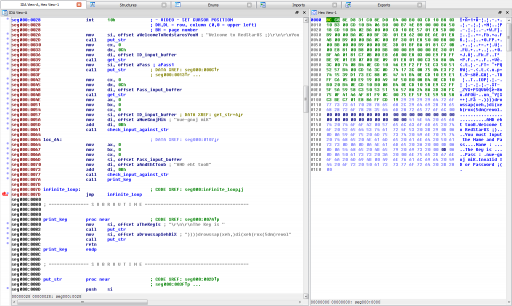
Let’s analyze the code in IDA.
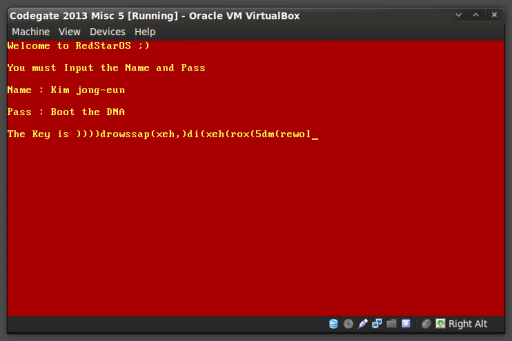
From the code analysis, we can easily see that the OS (a play on the North Korean Red Star Linux distribution) starts up and prompts for a username and password, expecting “Kim jong-eun” and “Boot the DNA”, respectively. If the user gets it wrong, the OS reboots; if the user is right, the key is printed.
The username and password are stored and compared in reverse. The key string is also stored in reverse, but the developer of the challenge doesn’t print it in reverse. To get this code to run in VirtualBox, you can dd the code to /dev/sda from a LiveCD of your choice after modifying the given sector 2 copy code to pull from the hard disk instead of the floppy (change the byte at offset 0x3d from 0x00 to 0x80).
Flag: lower(md5(xor(hex(id),hex(password))))